Much more than SBOMs: A Zero Trust Fabric for Continuous Assurance
Today we make RKVST available for public use with a free access tier so you can discover what a Zero Trust Fabric can do for you. From tracking software supply chain lifecycles to nuclear waste, RKVST is a powerful tool that builds trust in multi-party processes, when it’s critical to have high assurance in data for confident decisions.
But before going all the way you can start simple: tracking software releases and contents with SBOMs.
Best of Both: the quality and maturity of sensitive industrial processes with the speed and opportunity of software and connected operations
We’ve been working for a while now on private projects with some very interesting digital trust properties and maturing the platform to deal with them at the speed of software without compromising on important safety and security considerations.
For example, RKVST has been assessed by Sellafield Ltd to show significant potential to streamline nuclear waste operations, optimise real-time data exchange between organizations and improve traceability. Very simply it proves: What’s in the Box and Who did what when so that digital records can be relied upon and handling processes to proceed with speed and confidence.
While RKVST is built on leading edge cloud software including distributed ledger technology it is easy to access and integrate through standard REST APIs and familiar identity and access methods, removing a major barrier to adoption in existing businesses with a technology legacy. RKVST gets trustworthy data from one organisation’s toolchain into another’s preserving provenance, enforcing governance, and creating an immutable record of every event. Even when those events are flowing between completely different companies, toolsets, and IT regimes.
And this isn’t a niche nuclear problem: any business, at any stage of digitalization, can benefit:
- Buildings Compliance – what materials were used in construction, were they compliant at the time, what connected devices are installed, are they up-to-date?
- Maintenance Repair & Overhaul – which parts were fitted, what conformance to OEM specification, who did the repair?
- Autonomous Vehicles – which AI model is loaded, what training data was it given, is it approved to drive on the highway?
- Digital Twins – what connected devices feed data to the models, what is their status, who maintains them?
So then, if it’s good enough for nuclear waste, surely it’s good enough for software. Very few organizations handle nuclear waste but hundreds of thousands run software, and the value of knowing what’s in the box and where it came from is no less marked. More marked, in some ways, since software moves much, much faster.
Understanding Provenance
What ties all these use cases together is a supply chain challenge: information flows freely within businesses, but when it comes to distributing critical operating information across supply chain boundaries things get stickier. Information is under- or over-shared, can go missing, get delayed or destroyed at the boundaries of any exchange. In the event of a dispute data may go missing from remote databases, or at least become hard to find. Disputes over timestamps and data tampering are costly.
Put simply, there’s no easy way to automate valuable processes based on data arriving from the supply chain because there are precious few ways to take those data at face value.
What’s needed is a system that informs each party of the trustworthiness of data they’re using – a Zero Trust Fabric. With RKVST, provenance and process traceability helps understand someone else’s data quality, completeness, security posture and compliance, it makes it much easier to act upon with confidence. Especially so when you know you will always have access to those decision-critical data when audit time comes around.
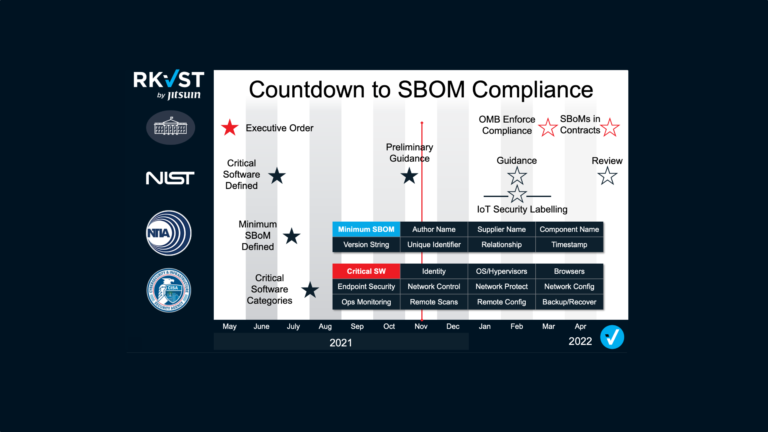
Software Supply Chain and Executive Order 14028
Executive Order 14028, released last spring, makes ambitious calls for steps forward in software transparency, exchange of threat intelligence (and note, this is not just CVEs!), and a drive towards Zero Trust architectures.
What’s very exciting about this is that with serious experience in hardware, software, cryptography, and IoT, our company was originally formed to address these issues! RKVST was originally designed to solve the fundamental questions of IoT security. Much more than simple firmware signing, we needed to know: what’s in the box? Where did it come from? What’s its identity? Who’s touched it along the way who could have compromised that identity? What has changed in the world since this was deployed to make something once trustworthy, now untrustworthy?
It’s an unfortunate fact of life that no matter how good cybersecurity widgets get, and how bold the promises of the latest hardware key store or AI network protection agent, attacks will always get through. Things will always degrade. Mistakes will always happen. So we decided to build a platform to help live with this reality and produce resilient connected systems.
Sounds familiar doesn’t it! Everything the Executive Order calls for is what we’ve been working on for years. We were delighted to see it, not just because it spoke to us but because now the whole industry has a totem around which to build and cooperate, and to defragment all the great work that has happened in so many groups over the past, some of which I have participated strongly in, and some of which I completely missed. Right now we have the opportunity to build a vibrant ecosystem of apps and services that enable connectivity and digitalization without losing that crucial security metadata.
SBOMs are the first step
So let’s go back to the beginning: before going all the way you can start simple: tracking software releases and contents with SBOMs.
We built the RKVST SBOM Hub as a single destination for people to find and fetch the public SBOMs they need. But critical software is often proprietary or licensed commercially, and neither publisher nor subscriber will want to reveal its full contents or lifecycle updates in full public gaze. While I subscribe very much to transparency and open source principles, responsible disclosure in the real world is a more subtle art.
Releasing RKVST Free provides an easy way for software publishers to navigate this tricky terrain by enabling them to control and govern exactly who sees which SBOMs and which lifecycle artifacts, while software consumers can be confident they’re getting all the information they need and work on the most up-to-date information from all their suppliers in one place. Producers can even index or announce important information in SBOM Hub and then distribute details on a need-to-know basis inside RKVST.
Those SBOMs can be produced by any CI/CD pipeline or software composition analysis (SCA) tools, and then consumed by security orchestration and automated response (SOAR) tools, neither of which need directly interoperate with the other, giving all participants free choice of which tools suit them best.
And once this first step is taken, and confidence in distribution assured, additional important information such as vulnerabilities, bundling and handling and cryptographic process artifacts can be added, still in one single verifiable log.
With developers realizing the power of RKVST to share trustworthy information about software assets and events, it begs the question, what other business processes would be easier if you could prove who did what when?
Get started
Sign in for RKVST Free and start building verifiable data about your critical assets.
Jon Geater, CTO & Co-founder, Jitsuin Inc